Encryption Key Management

Secure Your Data with Powerful Encryption Key Management Solutions
We understand the importance of secure and efficient encryption key management for your organization. Encryption keys play a critical role in safeguarding sensitive data and ensuring its confidentiality.


Key Features
Our comprehensive encryption key management service offers a robust solution to help you protect your valuable information effectively.
Centralized Key Management
Secure Key Storage
Key Generation and Rotation
Access Controls and Permissions

Range of Our Services
Our Encryption Key Management service offers numerous benefits to organizations seeking robust data protection and enhanced cybersecurity.

Centralized Key Management
Our platform provides a centralized repository for storing and managing encryption keys, ensuring easy access and efficient administration. You can securely create, store, and distribute keys based on your specific needs.
Secure Key Storage
We employ state-of-the-art security measures to protect your encryption keys. Our systems use industry-standard encryption algorithms to safeguard keys at rest and in transit. With our secure key storage, you can have peace of mind knowing that your keys are well-protected.


Key Generation and Rotation
Our service offers secure key generation capabilities to ensure the creation of strong and unique encryption keys. Additionally, we support key rotation, allowing you to periodically update your keys to enhance security and meet compliance requirements.
Access Controls and Permissions
We provide robust access controls and permissions management features, allowing you to define and enforce granular access policies. This ensures that only authorized personnel can access and manage encryption keys, minimizing the risk of unauthorized access.



Benefits With Our Service
Strengthen Data Security
Encryption keys are crucial for safeguarding sensitive information.
Simplify Key Management
This simplifies the overall key management process and reduces administrative burden.
Enhance Compliance
Compliance with industry regulations and data protection standards is critical for organizations.
Ensure Key Availability
This guarantees uninterrupted access to encrypted data when needed.

Our Clients

Why Choose Us?


Certified Info Security Auditor
Our CERT-IN and STQC certified testers follow a rigorous approach to identify vulnerabilities, assess risks, and test the resilience of your systems and networks.

Reliability
We are the 6th company to get empanelled with government bodies like CERT-In & STQC which are recognised and respected by industry professional and organisations.
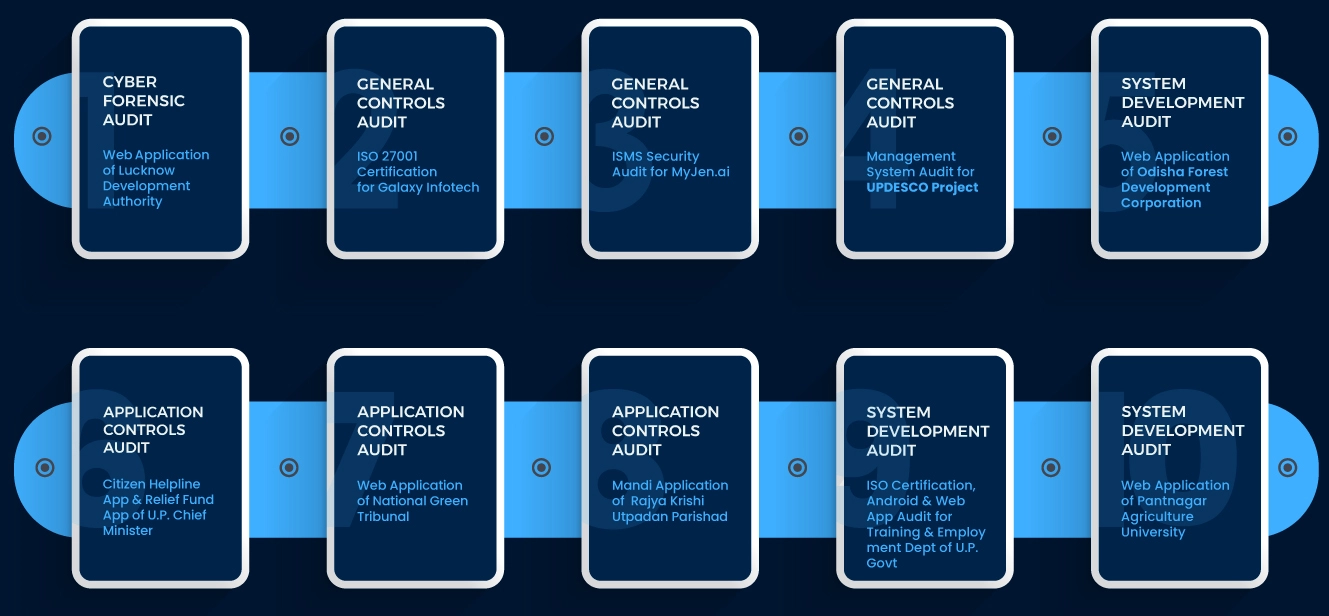
Projects We Delivered














Frequently Asked Questions
How does your encryption key management service work?
Our encryption key management service provides a centralized platform for creating, storing, and managing encryption keys.
How do you ensure the security of encryption keys?
We employ state-of-the-art security measures to protect encryption keys. This includes strong encryption algorithms, secure key storage, access controls, and robust authentication mechanisms.
Is your encryption key management service compliant with industry regulations?
Yes, our encryption key management service is designed to meet industry regulations and data protection standards.
Is your encryption key management service scalable?
Yes, our service is designed to scale with your organization’s needs. Whether you are a small business or an enterprise, our encryption key management service offers flexibility and scalability to accommodate growth and changing requirements.


